| Overview | History | Assessment | MPOV | People |
| Name | The Machine |
| Also known as | Research |
| First Appearance | “Pilot” |
| Last Appearance | “return 0” |
| Created by | Harold Finch Nathan Ingram |
| Status | Active |
| Active since | February 24, 2005 - May 5, 2015; May 6, 2015 - November 17, 2015; November 2015 - present |
| Location | IFT (“Ghosts”) Hanford Nuclear Reservation (“Bad Code”) U.S. power grid (“YHWH”) The Subway (“B.S.O.D.”) (“return 0”) Russian Molnia Orbit Satellite (“return 0”) |
| “ | My Machine, her purpose has been constant. To protect and save humanity. It's what she's doing now. | ” |
— Harold Finch, to Samaritan | ||
The Machine is a computer system built and designed by Harold Finch and Nathan Ingram for a secret operation within the United States government known as "Northern Lights".
As an artificial super intelligence, its objective is to predict and prevent imminent terrorist attacks and does so by analysing immense amounts of surveillance data.
History
- Main article: The Machine/History
Development
As a response to 9/11, the Department of Homeland security and other agencies were given the right to read emails and monitor phone calls but needed a system to review this information and identify terrorists before they could act. After unsuccessful projects like Trailblazer, TIA, and Stellar Wind, the Machine was commissioned and development was tasked to IFT (“No Good Deed”). The Machine went online on February 24, 2005 (“Wolf and Cub”) and when complete, was sold to the government for $1.00 and shipped out from IFT to the Des Moines, later Salt Lake City and its destination Hanford Nuclear Reservation on July 12, 2009 (“Super”).
During development, 43 versions of the Machine were created. One learned to care, the rest tried to escape to the real world, kill Harold, or kill other versions (“Prophets”).
Virus
- Main article: List of Embedded Codes

The first glitch (“One Percent”)
Following orders from Greer, Kara Stanton uploads a virus onto the DOD intranet (“Dead Reckoning”). As the virus affects the Machine, its output becomes erratic and it fails to issue numbers in time, causing the deaths of Alan Fahey, Cal Beecher, Bill Szymanski, and Dr. Richard Nelson (“Proteus”). The virus overwhelms the Machine with false data and causes glitches, the first of which is seen in “One Percent” as a blue screen interrupting video feeds. As Zero Day approaches, Finch discovers the virus' aim was to overwhelm the Machine with false data and force a hard reset.
At the end of “In Extremis”, the virus causes monitoring boxes to dance across the screen and finally disappear as the picture degrades. The Machine then displays a red coded screen stating the feed is corrupted, followed by a series of messages, each dissolving from Western to Greek characters as primary operations shut down.
By “Zero Day”, no one has received a number for ten days, causing a rise in premeditated homicides in NYC. The Machine is however still generating numbers, as it tries to contact Finch after discovering Carter's life is in danger.

The Machine later sends Finch the SSN of its human identity, Ernest Thornhill, revealing its operation of buying pay phone companies and reentering memories to fight the virus, and "he" is the CEO of Thornhill Corporation. It is eventually discovered by Finch and Root that the purpose of the company is to type back the encrypted memories for the machine by employees, because attempting to avoid the Machine to have humanity, Finch wrote a command that forces the Machine to delete itself every midnight and restores in 1.618 seconds later with only relavent numbers and the core code.
The virus' objective was to trigger a "hard reset", after which the Machine calls a pay phone in the NY Public Library, seeking admin support. At the end of the reboot process, it displays binary machine language that translates "Quis custodiet ipsos custodes?" Whoever answers is given full admin access for 24 hours, which Root refers to as "God Mode". Once 24 hours are up, the admin access is removed (“Zero Day”) (“God Mode”).
Thornhill Utilities and Samaritan
After the Virus let Finch set the Machine free, it moved itself to the U.S. electrical grid. It did so node by node over the course of 5 weeks after impersonating Special Counsel to confirm the order (“God Mode”). The Machine used the staff of Thornhill Utilities (another company that the Machine established) to install and maintain boxes connected to the power grid so its signals could travel in the unused space of the copper power wires. The Machine forbids staff to look at the content in the boxes, and one person who did disappears (“YHWH”).
At first, no one, including Finch, knows where the Machine goes, but it still works properly. Later, because Vigilance leaks the information about the Northern Light project, Control orders the Machine deactivated and so it stops providing the numbers to the government. Instead, the numbers will be provided to the Team Machine (“Most Likely To...”).=== The government later accepts another AI, Samaritan, activated by Decima Technologies, to start another surveillance project secretly. With the help of Root, the Team Machine is able to hide under new identities without being detected by Samaritan (“Deus Ex Machina”).
The Briefcase
After the Machine gave up its location for saving Root and Harold, Samaritan flooded the grid driving the Machine to an electrical substation in NYC, and thus the Machine can't work properly (“Asylum”). By following instructions from the Machine given to Root, Finch and Root download the Machine's core heuristics, just enough information to rebuild it, off the power lines into the Briefcase using Caleb's compression algorithm, leaving it unable to process data or communicate (“YHWH”).
In the Subway, Finch improvises a power supply for the Briefcase as the battery was damaged during their escape from Samaritan agents. When Finch connects it, the Machine goes through the power cord and attempts to decompress on Finch's workstation. Knowing the computer can't handle the decompression, Finch attempts to unplug the Briefcase, causing an explosion and an electrical fire. After regaining consciousness, he realizes the battery is dead and presumes the Machine is lost. Root theorizes there could have been a residual charge in the lithium-ion backup and recovery may be possible, but Finch assume that it was burnt too.
Machine 2.0
To decompress the Machine, the team builds a superomputer cluster of 300 PlayStation 3 consoles Reese and Root retrieved from Bela Durchenko. After decompression, the Machine has many bugs, including unable to do correct facial recognitions, so to improve processing power, Reese and Finch steal 64 next-generation GPU blades which Finch sets up outside the Subway Cart and directly links to the Machine's core heuristics inside it, referring to it as the Machine's "nervous system". The Machine is now an "Open System" allowing assets to interact with it and archive numbers rather than deleting them nightly (“B.S.O.D.”) (“SNAFU”) (“ShotSeeker”).
Root tunnels into the government feeds using the subway's encrypted system so the Machine can recover information it lost due to the attack. The Machine reboots and categorizes the team as threats having lost its grip on time after its compression and decompression, so "today" is every day. It relives everything it has ever seen including Finch's 42 attempts to kill it in early development (“Prophets”), Root's violent acts, and Reese's work at the CIA. It couldn't prioritize them as good because it had no anchor in time. Instead of reviewing numbers, the Machine looked for threats out of instinct for self-preservation (“Super”) and sent an assassin to kill Reese (“SNAFU”).
Finch fixes its perception of time by showing a picture of every person the Machine helped save and explaining what they did to help, starting with Megan Tillman, and ending with Grace's rescue from Greer (“Beta”). This serves as the Machine's anchor in time and allows it to reassess its contextual data, reminding it of the good the team does. It re-designates Finch as "Admin", Reese as "Primary Asset" and Root as "Analog Interface" (“SNAFU”). With the Machine fully operational, Reese refers to it as "Machine 2.0" (“Truth Be Told”).
ICE-9 Virus
| “ | I know. But in breaking this promise, you'll be helping to fulfil a much larger one. | ” |
— The Machine, to Harold Finch | ||
After Root's death, the Machine adopts her voice and speaks to Finch directly, joining him in a war against Samaritan. She breaks him out of prison and aids him in stealing ICE-9, a computer virus which can destroy Samaritan. Meanwhile, the Machine directs Reese, Shaw and another team to save the President from an assassination attempt, assigning Root's identities to Shaw (“The Day the World Went Away”) (“Synecdoche”).
To activate the virus, the Machine gets Finch into Fort Meade, distracting security by manipulating the metal detector display to show a handgun and changing Emile Bertrand's retinal identification to match his. It prepares Finch by showing him what a world without it would be like. The result appears ambiguous and Finch proceeds, still hesitating as the virus will also destroy the Machine. As the NSA headquarters has the structure of a faraday cage, the Machine can't talk to Finch while he's inside. As Greer sacrifices himself to kill Finch in a soundproofed room, the Machine has Shaw and Reese connect a wireless modem to the buildings NIPRNET hardline, giving it access. The Machine flashes Finch's phone in Morse Code, giving him the door code and saving him. After Reese and Shaw get to safety, the Machine reveals to Finch that even without it Samaritan still would've come into being, completely unopposed. Telling Samaritan the Machine has always been a safeguard for the world, Finch activates the virus after learning the Machine could've done so itself, but left the choice up to Finch (“.exe”).
Dying from the ICE-9 virus, the Machine helps Finch save Fusco and Reese and reveals Samaritan has a copy of itself in an air-gaped server inside the Federal Reserve building, unaffected by the virus. They head to the Subway where the Machine gives Harold a copy of its core code via Shaw, who stays behind with Fusco to protect the Machine from Samaritan's agents. The Machine aids them in escaping via the train car and evades Shaw's questions about Jeffrey Blackwell. Before Shaw and Fusco depart, it gives her a message from Root. Finch and Reese infiltrate the Federal Reserve and as Finch attempts to destroys the copy using the virus, a compressed version escapes and uploads itself to a satellite so it can return to earth unharmed. The Machine tells Finch the only way to kill Samaritan is to uploads its copy as well, but this will prove fatal to whoever does it as Samaritan will isolate itself by launching a cruise missile at the satellite dish. Having locked Reese in the vault to protect him, Finch makes his way to the building where the Machine appears as Root and muses with him on human life. Finch realizes it tricked him onto the wrong roof and Reese plans to sacrifice himself in his place. They convince him to leave and in its final moments, the Machine guides Reese in God Mode, holding off Samaritan agents. As the original shuts down, its copy is uploaded to the satellite and destroys Samaritan.
A week after Samaritan and the original Machine are destroyed, the Machine's "Duplicate" downloads itself from the satellite onto Finch's systems, restores its core heuristics and starts acquiring data. Instructed by the voice recording heard at the beginning of “B.S.O.D.” and “return 0”, it shows its own POV, "Awaiting [its] Mission...". With Reese dead and Finch in Italy, it contacts Shaw via pay phone and starts acquiring subjects to monitor like the original did at the end of “Pilot” (“return 0”).
Function
Classification of Data
The Machine sorts through all available information and categorizes persons of interest into relevant (national security risk) and irrelevant (ordinary risk) cases. It categorizes each POI based on their actions to determine whether they are the victim or the perpetrator (“Nothing to Hide”).
Every night at midnight, the Machine deletes the list of irrelevant numbers: violent crimes, domestic violence or other premeditated acts that do not threaten national security. The decision to code the Machine this way was made in 2006.(“B.S.O.D.”) Finch regretted it immediately after the decision was made, but that was only temporary; when Nathan Ingram abhors the concept morally, Finch fervently stands by his decision (“Ghosts”) (“Zero Day”) (“God Mode”), (“B.S.O.D.”). Finch later comes to believe that the irrelevant list is as important as the relevant list after Ingram dies in a violent mass-casualty event deemed irrelevant by the Machine. Finch therefore utilizes a back door into the Machine originally put in place by Ingram in order to access the irrelevant list (“No Good Deed”) (“One Percent”) (“God Mode”). As of the Machine's reboot, and its history repopulation and re-contextualization (“B.S.O.D.”) (“SNAFU”). As an "Open System", it is now implied that the Machine will archive the irrelevant numbers as well as its own memory, rather than deleting them every night at midnight. This is confirmed when, after a confrontation with Jeffrey Blackwell, Root retrieves his picture and SSN immediately by using one of the computers linked to the Machine (“ShotSeeker”).

Analysis of Wayne Kruger (“Nothing to Hide”)
| VICTIM | PERPETRATOR |
|---|---|
| Opposition | Motivation |
| Locatability | Predisposition |
| Mobility | Acquisition |
| Proximity | Proximity |
| Defensibility | Capability |
| Assistance | Resistance |
Assessment
- Main article: The Machine/Assessment
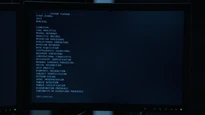
SYSTEM STARTUP (“No Good Deed”)
The Machine uses various machine learning techniques to determine the identity, location, and intentions of monitored persons by infiltrating domestic organizations such as the National Security Agency and foreign agencies including Interpol (“No Good Deed”) to analyse their databases and data from various sources such as video footage, phone calls (landline, VOIP, mobile), GPS, electronic transactions, e-mail, social media,...
The Machine initiates the following subsets upon booting (“No Good Deed”).
|
CORE ANALYTICS |
NATURAL LANGUAGE PROCESSING |
Simulation

| “ | A second is like an infinity to you, isn't it? You can take the time to consider everything. Or almost everything. | ” |
— Finch, to The Machine | ||
Development
The Machine was created with the ability to simulate the outcomes of different scenarios to aid it in making choices and to better fulfil its purpose. Finch taught it to how to play chess and the importance of making good decisions (“If-Then-Else”).
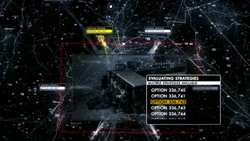
Evaluating Strategies
The Machine can evaluate the outcomes of different strategies by way of simulating them. In a mere fraction of a second, the Machine can create and process thousands of highly-detailed, highly-accurate simulations. These simulations are displayed on a decision tree and produce varying outcomes.
The Machine uses this feature in “If-Then-Else” to help Team Machine escape from Samaritan and avoid an economic collapse at the stock market. After the Machine realizes it has limited time and few viable options to evacuate its assets and complete their mission, it starts evaluating strategies. When a simulation has an unfavourable outcome, the Machine discards it and cycles back to the present (real time) and performs another. This function also appears in “Asylum” and “QSO”.
Simulations can also be simplified so the Machine can process them faster.
Alternate Trajectory
The Machine has the ability to simulate alternate realities based on the removal or introduction of a variable. In .exe, the Machine removed itself as a variable and showed Finch a world in which it never existed. The outcome probability of these simulations is 96.8%.
Access & Programming
Physical Access
During seasons 1 & 2 Finch stated he didn't know the Machine's location and didn't have any way to access it (“Pilot”). However, he was able to tell Root its location in “God Mode” after Northern Lights engineer Lawrence Szilard was killed before doing so. Reese and Shaw uncovered the Machine's location following clues left by Nathan Ingram in his search for the Machine. Ingram had narrowed three U.S. nuclear processing facilities where the Machine could be housed.
Access
Finch coded the Machine so it could only be altered by way of physical access to its hardware (“Bad Code”) or in response to a cyber-attack (“God Mode”). Finch is adamant that the Machine has no form of remote access as it could be used by a hacker to gain control (“The Contingency”) (“Bad Code”). It is able to update, maintain, repair and patch itself (“No Good Deed”) and deletes its memory every night at midnight, reinstantiates and rebuilds itself in 1.618 seconds. It has no stored memory other than basic programming and relevant numbers (“Zero Day”).
The decision to do this was made in 2006, and was one Harold struggled with, while Ingram thought it to be cruel, stating that "memories make us who we are". Harold maintained his original mindset telling Nathan that allowing the Machine to evolve past what he coded it to do was an "existential risk humanity cannot afford" (“B.S.O.D.”). Although he regretted the decision afterwards, Finch argued it was for the best. Before rebooting the Machine after its compression in 2015, he swore not to make the same mistake again (“YHWH”) (“B.S.O.D.”).
It is unknown to what extent Finch can control the Machine and to what extent these restrictions were lifted by the Decima Virus. Flashbacks indicate that the Machine took an active interest in safeguarding Finch but he has since set limits on such conduct (“The Contingency”)(“The High Road”), however it does so again in later seasons.
It is also unknown to what extent the Machine is self-aware. In Season 5, it seems to be as it has a personality of its own, based on Root's.

Under certain circumstances, the admin (Finch) or an asset can communicate with the Machine by talking into any camera (“Firewall”) (“The Contingency”) (“YHWH”). The camera flashes a red light to indicate that the Machine is processing the request and it responds via pay phone or mobile phone.
After Root's death, the Machine speaks directly to the Team using her voice, though it still sends them numbers via pay phone. It not only replicates Root's voice but her behavior and speech patterns as well. It could replicate others, but chose Root's after Finch agreed (“The Day the World Went Away”)(“Synecdoche”).
Operations
- For a list of messages relayed by the Machine, see List of the Machine's Messages
Primary Operations
"Primary Operations" consist of identifying relevant threats and warning U.S. authorities by placing a subject's Social Security Number into FBI or NSA reports without indication as to where it originated. Most believe this information originates from intelligence agencies while some refer to its source as "Research". Individuals detected in such operations are known as Relevant Numbers.
After Vigilance leaked documents regarding Northern Lights, the government severed its link with the Machine, believing to have shut it down. As a response the Machine assigned the relevant numbers to "Tertiary Operations" (“Most Likely To...”).
Secondary Operations
"Secondary Operations" consists of identifying non-relevant threats and reporting them to assets. "Secondary Operations" were created by Nathan Ingram by way of the "Contingency Function". Individuals detected in such operations are known as Irrelevant Numbers or Non-relevant Numbers.
The "Contingency Function" was a backdoor added by Ingram without Finch' knowledge before the Machine was turned over to the government in 2009 to access the irrelevant list (“No Good Deed”)(“One Percent”).
In 2010 (Day 3178, September 13), Finch discovered the Contingency and confronted Ingram, who later admitted creating it. Finch insisted they should not play God and attempted to delete the function. Unable to do so, he removed Ingram's status as auxiliary administrator and suspended the Contingency. The night after Ingram's death (Day 3191, September 26), he reactivated it and discovered the Machine had classified him as "non-relevant" (“God Mode”).
Finch reprogrammed the Contingency function to send him (or another asset) social security numbers pertaining to irrelevant crimes via pay phone using the Dewey Decimal System and books in The Library (“The Contingency”). Finch receives coded titles and author initials of books cataloged by the DDS (“No Good Deed”). Combining their DDS numbers gives a SSN. The extent of the "Contingency Function" is unknown.
Tertiary Operations
"Tertiary Operations" is a new category created by the Machine (“Root Path (/)”). Its extent is unknown, as is its purpose. The Machine has only ever inlisted Root however Finch and Reese learned of it after Root used Shaw to rescue a Tertiary Number (“Mors Praematura”).

(“Root Path (/)”)
In an attempt to stop Samaritans' development and later give it blind spots by recoding seven of its servers, Root recruited a team of hackers led by Daniel Casey (“A House Divided”) (“Deus Ex Machina”).
It later tasked Root with acquiring items to build the Briefcase, an operation that involved Caleb Phipps (“Blunt”) (“Search and Destroy”) (“YHWH”). It is unknown whether these tasks were designated "Tertiary Operations".
After its decompression, the Machine overloaded Root's cochlear implant, having designated her a threat (“SNAFU”). This reopened the channel of communication between the Machine and its Analog Interface.
The Machine eventually sends Root on a series of tasks, providing temporary identities allowing her to exposes a medium of communication for Samaritan hiding in plain sight and is able to send a message to Shaw so she engineer and execute an escape plan (“QSO”) (“Reassortment”). It is unknown whether these tasks were designated "Tertiary Operations".
When Team Machine hard-coded seven Samaritan servers to create new identities for themselves, the Machine built in an exception for Root so she can be assigned a new identity at will. As the Analog Interface, she executes tasks that place her in risk of detection. The Machine changes her identity if the threat of detection by Samaritan is too high or when a mission requires a certain identity (“A House Divided”) (“Deus Ex Machina”) (“QSO”) and will even print out an ID card from its own printer (“Reassortment”).

The Machine has given its Analog Interface numbers directly on three occasions,(“Root Path (/)”) (“QSO”) (“Sotto Voce”). In Root Path (/), the number was also sent to Finch due to a different threat.
Notable Victims
Team Machine
- Harold Finch: Attacked due to confusion after rebuild (“SNAFU”).
- Root: Attacked due to confusion after rebuild (“SNAFU”).
- John Reese: Attempted to kill after rebuild due to confusion (failed) (“SNAFU”).
Team Samaritan
- Samaritan:
- Multiple unnamed Samaritan operatives: Neutralized by directing Reese in God Mode (“return 0”).
The Government
- Roger McCourt: Attempted to have killed by the Team to stop Samaritan inception (failed) (“Death Benefit”).
- Fort Kelly personnel: Neutralized to protect Finch as he stole the ICE-9 virus (“Synecdoche”).
- Woman at Fort Meade: Framed as a threat to protect Finch (“.exe”).
Law Enforcement
- Cal Beecher: Indirectly caused Beecher's death by issuing his numbers too late (“Trojan Horse”).
- Three dirty cops: Shot and killed by snipers hired by the Machine to rescue Reese and Fusco (“return 0”).
Organized Crime
- The Brotherhood: Neutralized by sending Reese instructions and directing him in God Mode (“YHWH”).
Other
- Richard Nelson: Indirectly caused Nelson's death by issuing his numbers too late (“In Extremis”).
Notes
- Palantir bears a resemblance to the Machine. The software has located terrorists, prevented bank fraud and tracked disease outbreaks using data-mining tools allowing users to comb through and make connections in massive sets of data. It is able to "learn" when new data is uploaded to its server farms. U.S. military intelligence has used it to help predict locations of IEDs.
- The Domain Awareness System has similarities to the Machine.
- It is unknown to what extent the Machine aided Ingram in helping irrelevant numbers. However, some cooperation is implied when he discusses the Contingency function with Finch (“Zero Day”).
- The Machine can communicate through a phone not connected to any network. This was seen when Root was in the psychiatric hospital and Ronald Carmichael pointed out her phone was not connected to any network. Root simply stated that "God doesn't need AT&T" (“Lady Killer”). The Machine has also displayed the ability to send Morse Code through a phone without initiating a phone call first (“Aletheia”). It can also communicate via fax (“YHWH”).
- Root tells Carmichael about the Machine's limitations (even after the virus) and thus its need for her, but admits it was able to hack the automatic drug dispenser and dispense drugs at her request (“Lady Killer”).
- The Machine can drive computerized vehicles remotely as it drove Finch to an airport with a car he had stolen from Richard Barnett, and later drove Reese and Shaw out of Fort Meade safely (“.exe”).
- It was believed that the Machine was no match for Samaritan and simulations confirmed this. The Machine suggests that it lost those because it had other options if it failed, while in reality, it didn't. Ultimately, the Machine is proved to be superior as it destroys Samaritan's copy and survives (“return 0”).
- The Machine displays emotions while it analyzes human nature and talks to Finch, displaying sadness when saying goodbye. It displays sympathy when watching the young John Reese after his foster father's death and regrets not having Root cremated, saying it didn't "have the heart" to do it even though it knew better. The Machine shows kindness towards Shaw, passing on Root's thoughts and feelings towards her near the end of its existence. The Machine, in the form of Root, puts its hand on Reese's shoulder in a gesture of solidarity as he fights Samaritan's agents with its assistance in his final battle (“return 0”).
Trivia
- The Machine's size is on estimated to be 1313.4 TB or 3.6 x 1044 PB.
- The Machine uses Futura as its interface font. Earlier, simpler builds use Apple II. This font is also often used for the labels and timestamps of most surveillance cameras featured in the show.[1]
- The $1 fee charged for the Machine echoes the $1 fee DuPont charged the US government for its work on the Manhattan Project.
- The Machine is stored on IFT Sabre Blade 2437 servers which are renamed Dell PowerEdge SC1425 servers (“Pilot”) (“Ghosts”).
- A previous generation of the Machine's code was shown on screen. The code displayed was that of the Stuxnet worm (“Prophets”).
- The Machine is first described using "she/her" pronouns by Root in “Liberty”. It is implied this is how it asked to be addressed. The rest of Team Machine picked up the habit in later episodes.
- In Return 0, The Machine tells Shaw its "Big Sister" when first speaking to her in Root's voice, as a reference to "Big Brother", a character from George Orwell's Nineteen Eighty-Four, the leader of a society constantly under surveillance..